It has been over one year since I published my article on Japanese feature phone game preservation, and so much has happened in that time! From discovering new hardware exploits to finally cracking SD card encryption, the small but dedicated preservation community has made incredible strides towards preserving these special pieces of Japanese gaming history. Without further ado, let's survey the state of Japanese feature phone game preservation in 2023!


Left: Final Fantasy VII-themed P900iV phone (image credit to NaoyaShinota). Right: pop singer Hikaru Utada advertising DoCoMo feature phones
For those who need a quick refresher, Japanese feature phone games (keitai games) were video games developed for Japanese feature phones, better known as "dumbphones." These phones used mobile internet services to connect users to many utilities, including storefronts for purchasing video games. The three main services were DoCoMo's i-mode, AU/KDDI's EZweb, and SoftBank's Yahoo! Keitai. Major game developers like Square Enix and Capcom developed wholly original games for these devices, from a prequel to Final Fantasy VII to an exclusive side story for Persona 3! All of these game services have shut down, eradicating thousands of keitai games and stranding any remaining copies on aging flip phone hardware. This has created a time-sensitive game preservation crisis. For more background, I recommend reading my first Hit Save article.
Preserving I-Mode Games Through Appli Archives and G-MODE Archives

On September 28th, game history was made when a commercial DoCoMo i-mode game, Flyhight Cloudia, was preserved for the first time! However, the method in which this game was preserved was very unusual. G-MODE originally released this game for Japanese feature phones in 2004. In 2011, they rereleased it as part of their G-MODE Archives, which are recreations of their past keitai games. Most G-MODE Archives releases are Unity recreations, but an early Android rerelease of Flyhight Cloudia contained Java game files and a DoCoMo i-appli runtime! The .jar file was encrypted and in a specifically optimized format which contained internal bytecode of IBM J9 virtual machine. usernameak converted the .jar file back to normal bytecode, making it playable. It is important to note that this isn't the original game file from a phone. Nonetheless, this set the stage for more exciting keitai game preservation developments!



From 2014 to 2015, HAMSTER Corporation released Appli Archives, a collection of keitai games, on PlayStation Mobile. They released a total of 51 collections, each having between one to four games from publishers like G-MODE and Jaleco. Interestingly, each Appli Archive collection contains their games' original DoCoMo i-mode game files. PS Mobile games use PSSE encryption, so in order to obtain the original game files, one needs to get a license key from a game copy. In addition, the collections were internally emulating the server it was trying to download files from, meaning some modifications had to be done to the files to get them playable on an emulator. This is where user MemoryHunter stepped in, disassembling the game files and using XAMPP to make a local server. By switching the game's server to this new local server, the game files were able to be "downloaded" to their empty scratchpad (.sp) files.
As of this writing, eight Appli Archives collections have had their games preserved, such as City Connection DX and Burgertime. Most of the games are minigames or arcade ports.
Decrypting I-Mode Games on SD Cards
In the past year, the keitai game preservation community has obtained all the resources necessary to completely decrypt i-mode games on SD cards. When i-appli gets moved from a phone to a microSD card, it becomes encrypted with the C2 (Cryptomeria) cipher and CPRM. It is important to note that i-appli can only be moved to an SD in the presence of a UIM (akin to a SIM card), and not all phones support this function. There are quite a few items needed to crack the CPRM, most notably an s-box, a device key, and a bind ID. The s-box is universal, and it was discovered on a Japanese Samsung Galaxy S2 by usernameak about two years ago.
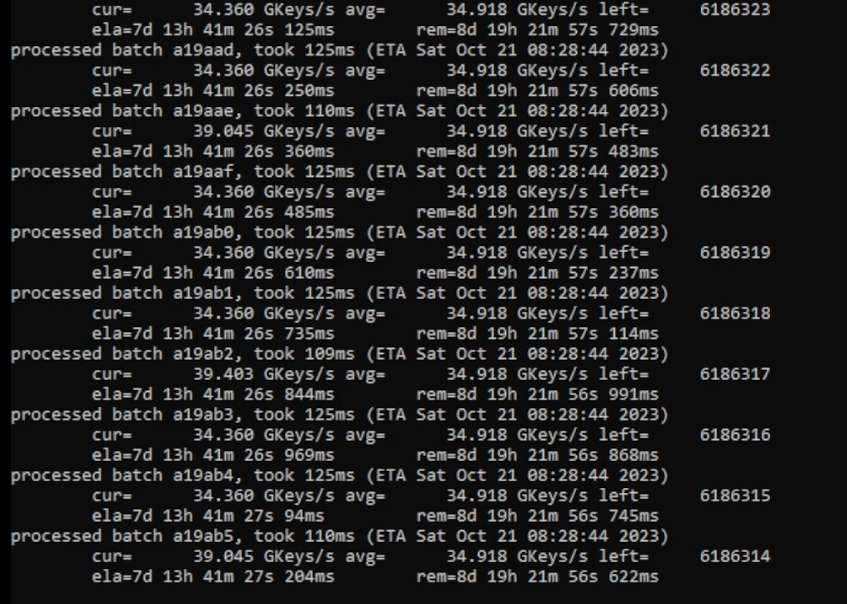
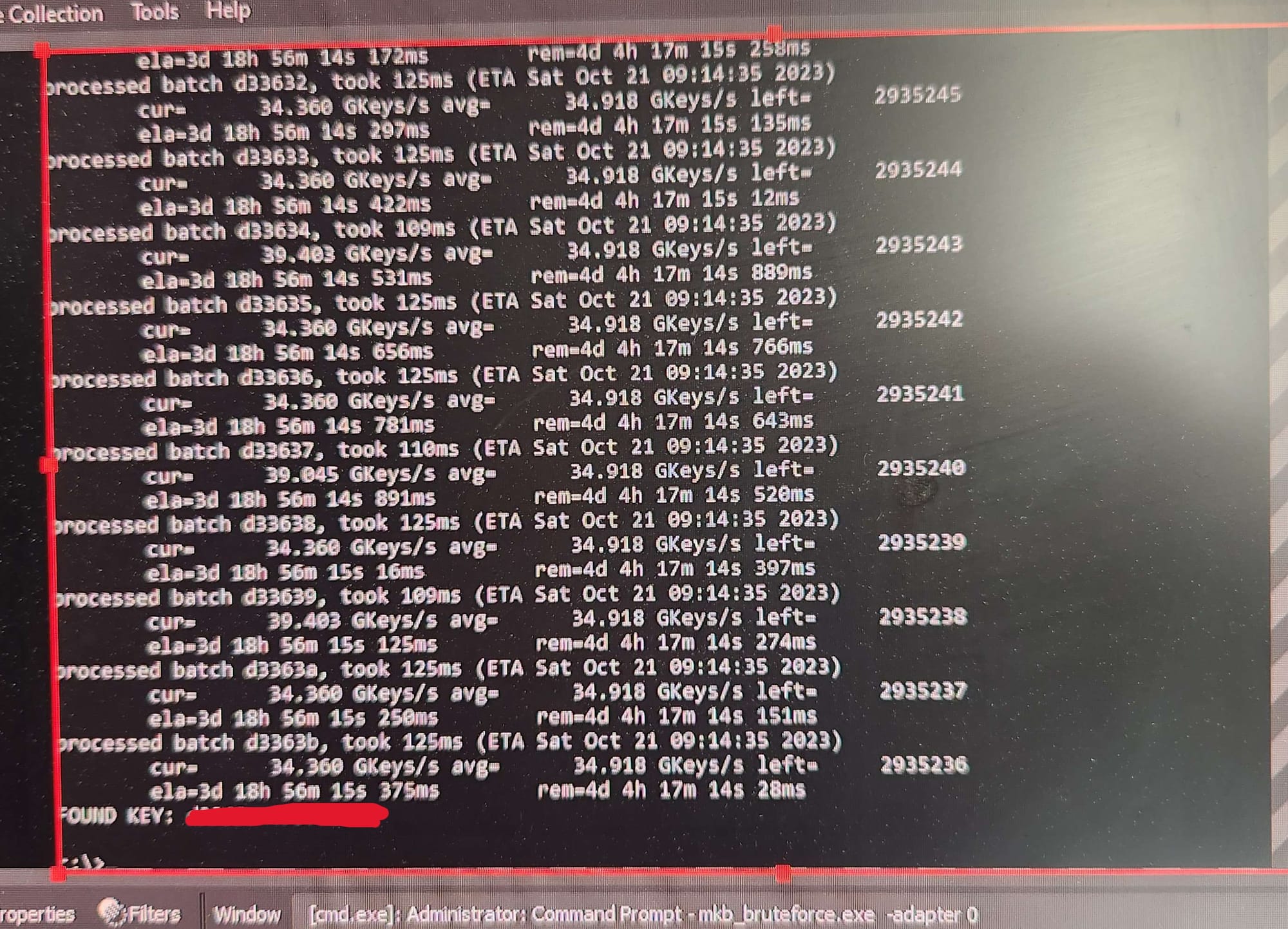
Left: The bruteforcing tool running on GoodTofuFriday's GPU. Right: the device key is found! (image credit to GoodTofuFriday)
However, obtaining a device key proved to be more difficult. It originates from the phone, and it's used to unlock the media key and media unique key, both of which are necessary to decrypt the game files. On September 26th, user GoodTofuFriday set out to bruteforce a device key, utilizing a program by usernameak and XerTheSquirrel. Equipped with his AMD Radeon RX 7900 XTX, he bruteforced 34 billion keys a second, finally obtaining a key 20 days later. This was a massive step towards finally decrypting i-mode games on SD cards, especially since the device key is universal and can be used across SD cards.
But there was still one more hurdle: bind ID. Users are still figuring out how exactly it's generated, but it's hypothesized to come from the UIM and the game itself. As such, there were initially fears that SD games without their UIMs couldn't be decrypted due to the bind ID's possible derivation from a UIM. Luckily, bind ID can be derived from the SD card's device unique key (different from the device key). A device unique key can be bruteforced, taking a significantly shorter amount of time than bruteforcing the device key. However, it is prone to false positives, as the tool is bruteforcing against 56 bits of known plaintext with a 56-bit key. Therefore, the bruteforcing process is more about ruling out potential keys than finding one. The right key can be anywhere in the keyspace.

Screenshots of Rockman Tennis
Using a modified version of usernameak's aforementioned bruteforcing tool, XerTheSquirrel and GoodTofuFriday bruteforced an SD card's device unique key on December 30th. Both users started from opposite ends of the keyspace. This card contained four encrypted Rockman games. It took them three days while finding one false positive, which was ruled out. The device unique key precombined the bind ID and the media unique key, allowing for Rockman Tennis and the fifth chapter of Rockman DASH 5 Islands to become the first decrypted i-mode games on an SD card.
However, there are some technicalities to the bind ID. It is also not universal like the device key and s-box; it is specific to the SD card it came from. In addition, it is per SVC folder – meaning it is per application that owns the game files. For example, the fifth chapter of 5 Islands was present in the same SVC folder that contained Rockman Tennis. However, the rest of 5 Islands' chapters are in a different SVC folder because they are additional data owned by 5 Islands and not the phone's system. As such, its bind ID will need to be derived by a separate bruteforcing of that SVC folder's device unique key.
There still needs to be more research done on how the bind IDs are generated. Once that is known, users can develop alternative methods to finding it. At long last, i-mode games on SD cards are finally decryptable!
Hacking DoCoMo Phones with a Debug Cable
For years, it has been difficult to hack into Japanese feature phones, especially DoCoMo i-mode phones. They use a wide range of proprietary chips, and their filesystems are also highly customized. There are also very few data sheets, schematics, service manuals, and debugging software.
There have been some exceptions. Many LG DoCoMo phones used a well-documented chipset and had their JTAG pinouts found, so they are dumpable in theory. In fact, many of them had their firmware dumped a decade ago, albeit most of said dumps have not been archived online. In addition, two i-mode Motorola phones, the M702iG and M702iS, can have their firmwares accessed through USB. They are based on the internationally-released Motorola RAZR V3XX, so there was more documentation surrounding them compared to the other Japanese-exclusive phones. Finally, user Yuu was able to dump a 2015 Panasonic DoCoMo phone (P-01F) by unsoldering its eMMC and analyzing it with a chip programmer. This process was repeated on two Panasonic Softbank phones, the 301P and 401PM.
However, the keitai game preservation community was still at a loss regarding phones by other manufacturers. It appeared most hardware hacking methods were on a model-by-model basis. This all changed in October, when users Yuu and Xyz discovered an exploit that would change the dumping trajectory for Panasonic and NEC DoCoMo phones.

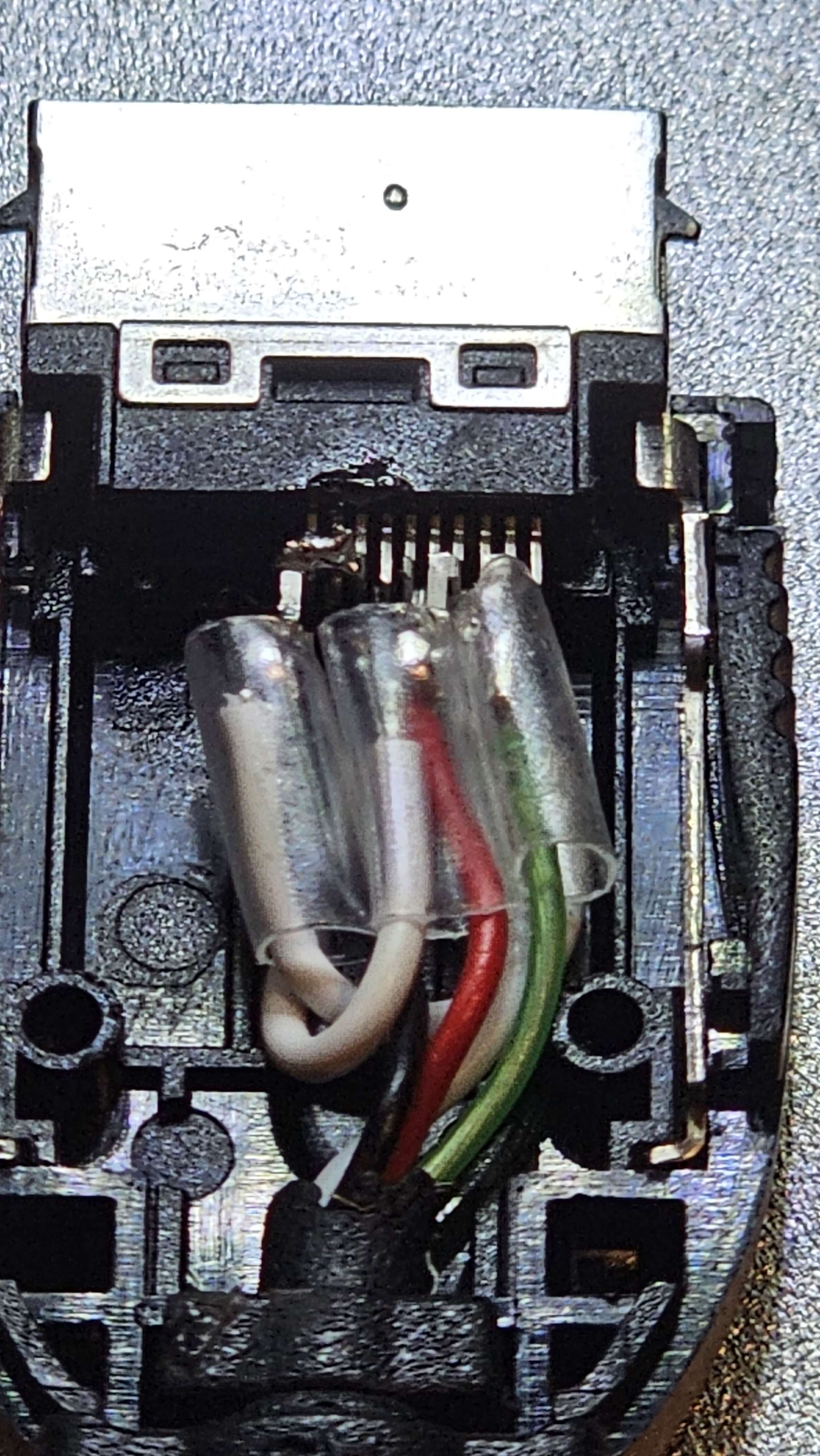
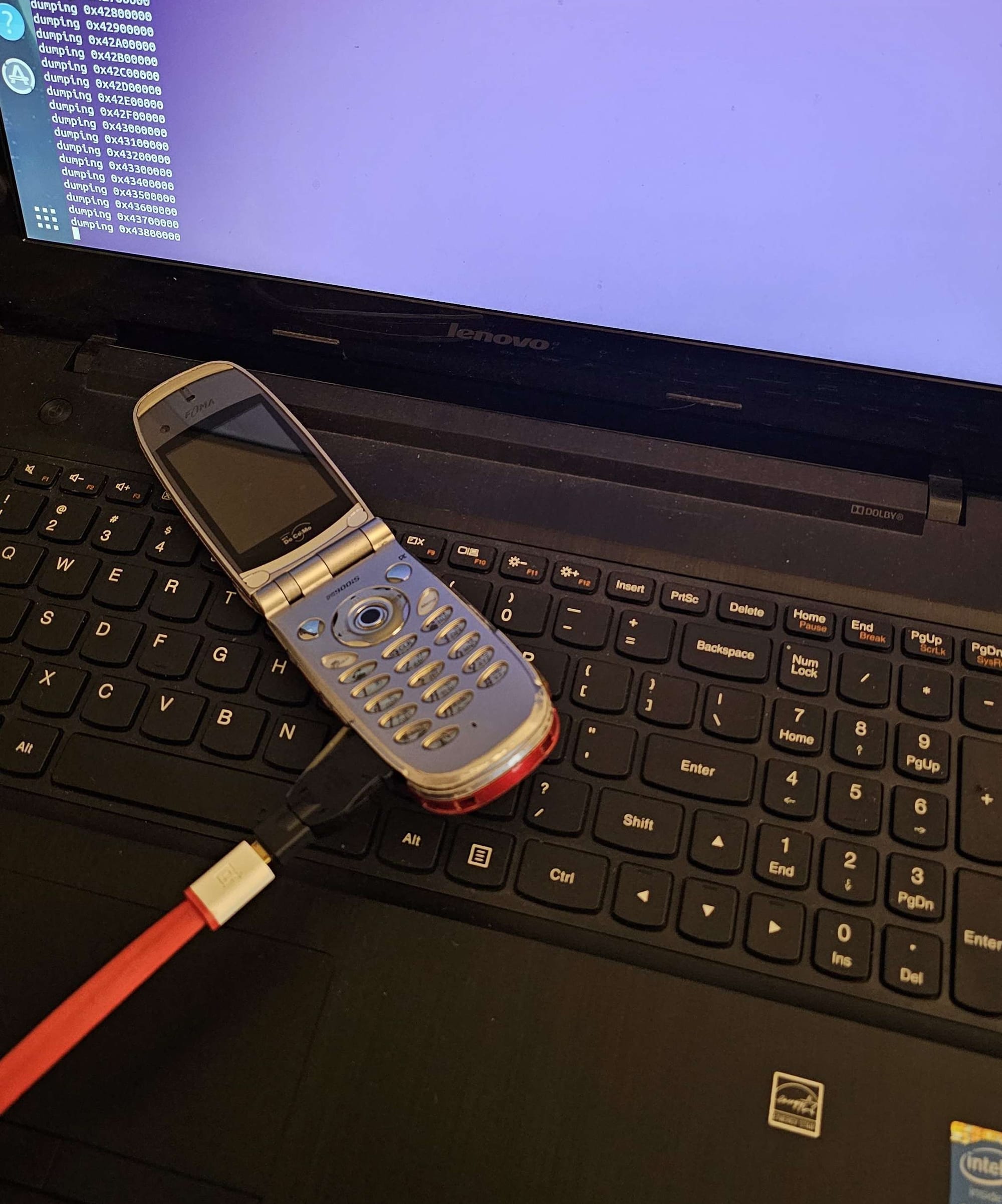
Different steps of the debug cable method (image credit to LNRC)
Yuu used a soldering iron to short the 4-5 and 8-10 pins on a standard FOMA to micro USB cable. After analyzing Yuu's P-01F dump and an NEC unlocking tool, Xyz figured out a protocol to work with Yuu's modified pinout. When using this modified cable and custom-made Linux scripts, some NEC and Panasonic phones booted into IPL mode, which is a kind of testing mode. This dumped the internal memory contents of a few DoCoMo phones. It is important note that the custom scripts are crucial to getting this method to work; dumps don't simply fall out of a cable. For NEC and early Panasonic phones, Xyz used the NEC unlocker tool to find specific commands to unlock the phone's memory and payloads to dump the phone's flash. The debug mode for later Panasonic phones is more locked down, but Xyz exploited a vulnerability in the USB stack to gain access. There's plenty of work behind the seemingly-simple process of plugging in a cable!
With the help of other Kahvibreak server members, Xyz developed the ktdumper tool, which supports a number of Panasonic and NEC DoCoMo phone models. This tool dumps a compatible phone's filesystem, allowing users to analyze it. The work doesn't stop there, as some phone models use different flash translation layers (FTLs) – software that makes filesystems compatible with flash memory. For example, the P-06C uses Samsung FSR, while the P903i uses XSR1. Some FTLs are easier to figure out than others, so even if a phone's filesystem is readable with a debug cable, there may still need to be work done on its FTL before any games are preserved.
Furthermore, the success of the debug cable method doesn't work for all phone models. Its success hinges on if the phone model uses a certain type of bootloader and IPL. This is why the method has only worked on certain Panasonic and NEC DoCoMo phone models; other manufacturers like Sharp and Fujitsu do not have these exact components. Interestingly, this method also works with a select few Panasonic SoftBank phones by coincidence (301P and 942P); they happen to be built like their DoCoMo counterparts.




A sample of some i-mode games that have been preserved with the debug cable method
This new method has resulted in an i-mode game preservation renaissance. More i-mode games have been preserved in the past two months than there have been in the past two years. Many preloaded and paid games have been dumped, from puzzle games like Puyo Puyo Fever DX to silly freeware like Nose Hair Expert!
Most notably, eight lost MegaMan games were preserved from a P-06C using ktdumper and a debug cable. Among those games were the full versions of Rockman.EXE Phantom of Network and Rockman.EXE Legend of Network. They were initially thought to be partially complete versions of the games, as the phone's original owner said she did not purchase the full games. However, both EXE games were actually paywalled full games; a subscription check could only be imposed when the games were on the phone. In addition, the fifth chapter of Rockman DASH 5 Islands was discovered in the phone's deleted files. Its remaining chapters remain encrypted on an SD card. This was a major milestone in MegaMan game preservation, as well as keitai game preservation at large. For more information on these games, feel free to read my article over at Rockman Corner.
Gameplay of Dirge of Cerberus Lost Episode's preserved demo
In addition, the demos for Dirge of Cerberus Lost Episode - Final Fantasy VII and Final Fantasy IV The After Years were preserved from a P903i. The Lost Episode demo was preloaded, while The After Years demo was a commercial game. On December 25th, the Kingdom Hearts Coded demo was preserved from a P-01A. With ktdumper's compatibility list expanding to include most Panasonic DoCoMo phones, more i-mode games will be preserved than ever before.
Hacking DoCoMo Sharp Phones

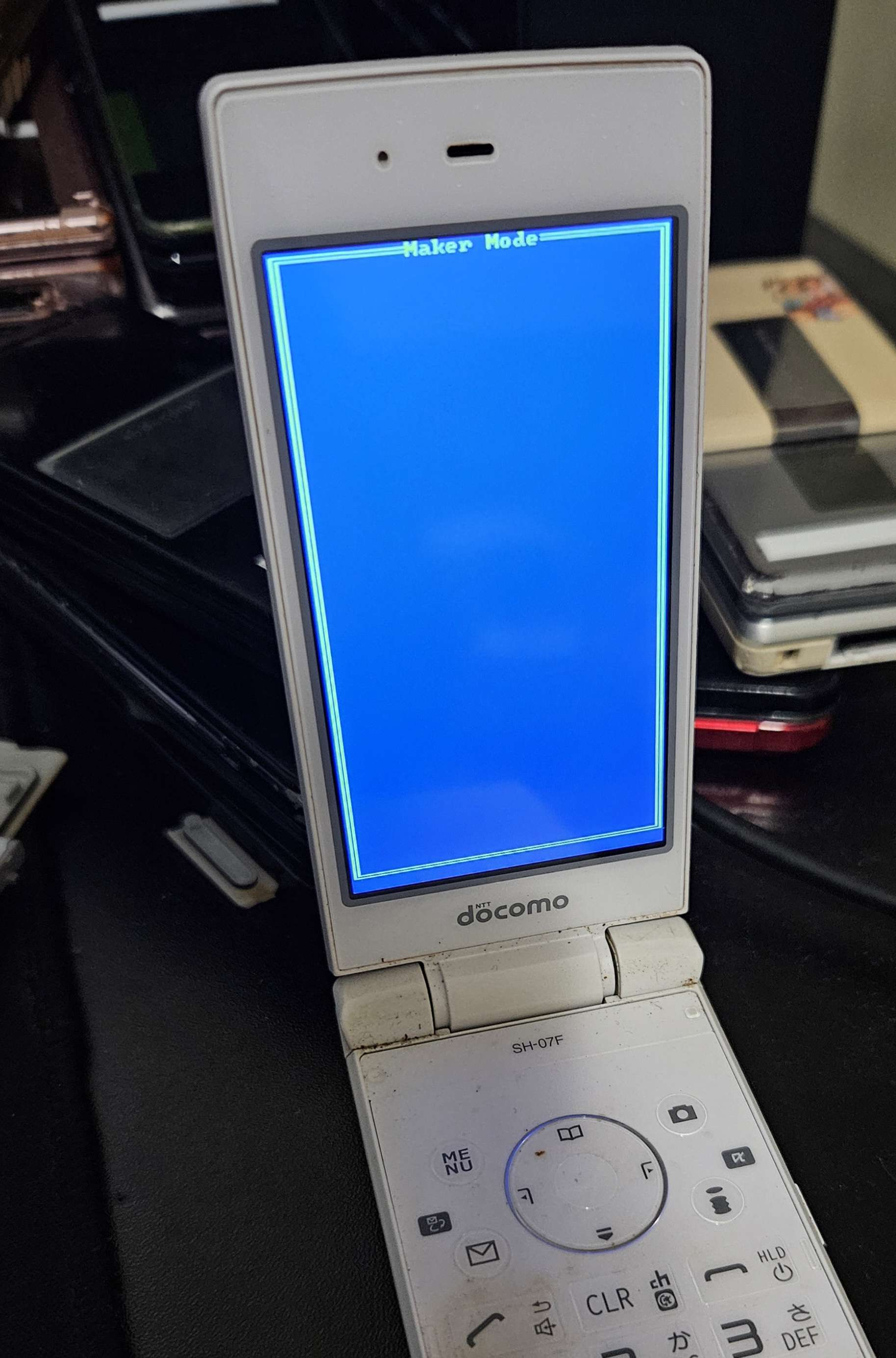
Left: SH-03E menu icons from its system partition. Center: the SH-03E being dumped via eMMC (image credit to LNRC). Right: the SH-03E in "maker mode" (image credit to Xyz)
After Xyz successfully dumped two DoCoMo Panasonic phones via eMMC, some users wondered if the same could be done with DoCoMo Sharp phones that used eMMC. On December 9th, a DoCoMo SH-03E phone was dumped by LNRC and Good TofuFriday. GoodTofuFriday unsoldered its eMMC, and LNRC analyzed it with an XGecu chip programmer. This gave people access to a Sharp phone's Symbian filesystem for the first time. The phone uses a custom compressed filesystem for system files, but it uses FAT32 for its user data. This means its game data can be easily unpacked with TestDisk. Initially, the custom filesystem was unreadable, but usernameak discovered its tools' source code in the SH-03E's open source software. He then discovered a prebuilt version of the tools in the Symbian^3 SDK, allowing the entirety of the phone to be read! The SH-07F phone is built extremely similar to the SH-03E, so it can be dumped in theory. Xyz believes these recent developments could lead to a promising exploit for these to phones, and by extension, other contemporary Sharp DoCoMo phones.
Xyz was also able to use the custom debug cable and a special command to put the SH-03E into "maker mode." This is a different kind of test mode than IPL mode, as it runs from Symbian and not the phone's bootloader. At the time of writing, it is not known if this mode is useful or not.
EZweb Game Preservation
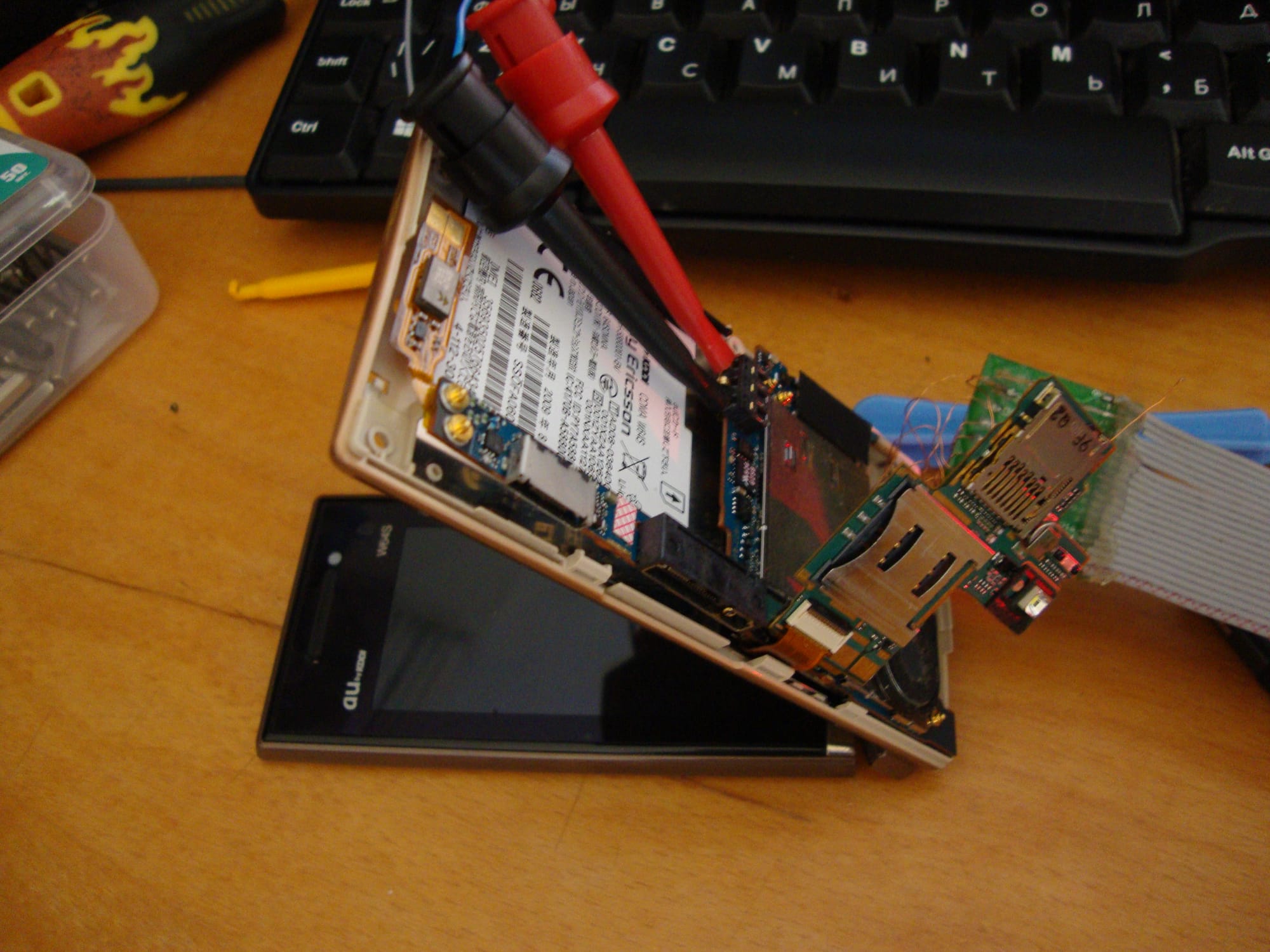
AU phones face similar barriers to hacking. While most of them use Qualcomm chipsets, they use various types of complicated and proprietary filesystems. These phones do not enable the CPU while turned off and charged; they to be turned on and powered by a battery or a lab PSU. Therefore, it is a finnicky process to monitor all of the phone's internals. In addition, AU phones use multiple flash memory integrated circuit (IC) to store data. They can also use multichip packages with several NOR or NAND banks that cannot be switched while dumping with a JTAG box. This is in stark contrast to Western Qualcomm-based phones, which only used a single IC or a multibank IC with a common memory area. To make matters worse, a lot of EZweb games have online license checks, which are harder to circumvent than DoCoMo games' license checks because most EZweb games run on BREW and not Java. BREW applications use native code, which is harder to reverse-engineer.


Left: finding JTAG pins on a Sony-Ericsson W53S using Riff-Box. Center and right: the destructive method of dumping a Sony-Ericsson SO005 (image credits to Kraze)
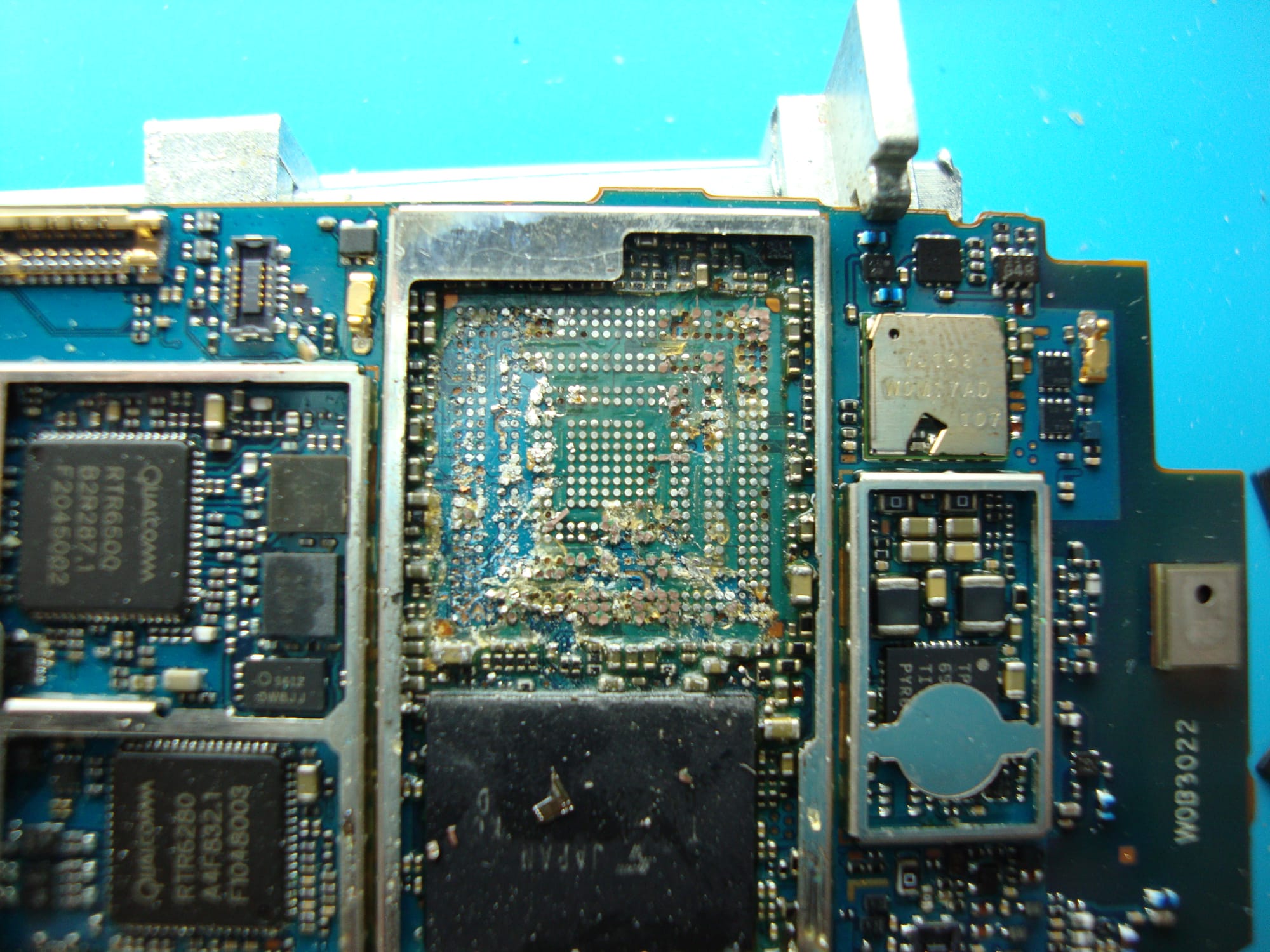
The first step of dumping an AU phone involves finding its JTAG pins, which are usually present on unlabeled test points. This involves desoldering the phone's system-on-chip (SoC) and finding relevant testpoints on the board. Since the SoCs are glued to a base with epoxy, desoldering is usually irreversible. A less destructive way of finding JTAG pins is through the use of a tool like JTAGulator or JTAGenum. After finding the JTAG pins, the next step is to leverage the phone's JTAG interface and dump its NAND chip through a flashing interface called RIFF Box. Finally, users try to identify known filesystems and extract them from dumped images. As of this writing, it is possible to extract the images of phones that use the FUGUE FAT filesystem or Qualcomm's EFS2 filesystem. Most Sony-Ericsson phones use FUGUE FAT, and phones like the CA005 use EFS2. Toshiba and older Casio phones cannot be extracted yet.
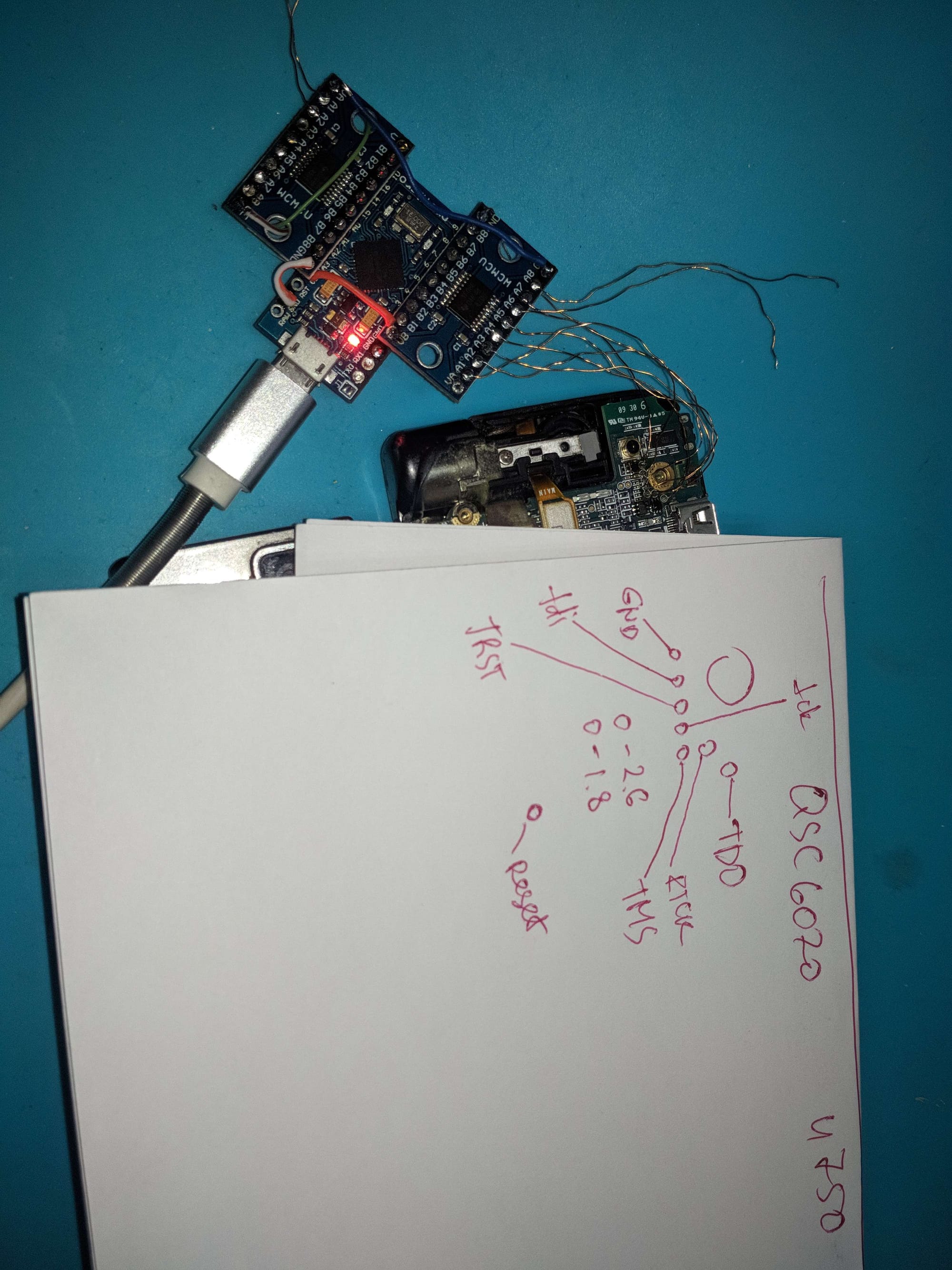
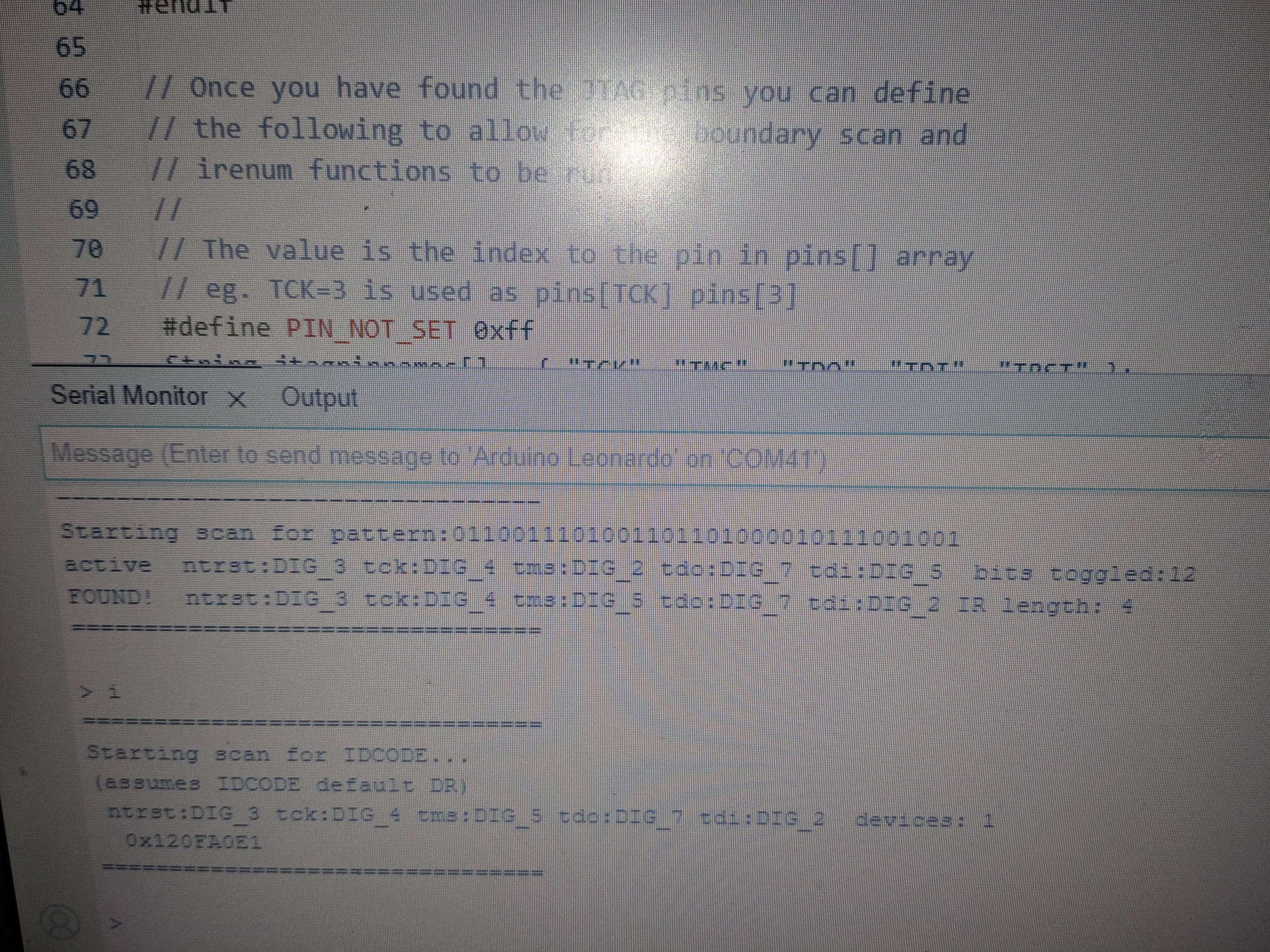

Kraze using JTAGenum to dump a Qualcomm-based phone (image credit to Kraze)
According to Kraze, a user who is extremely experienced with hacking Japanese Qualcomm-based phones, 19 AU phones have been tested to varying degrees of success. Only eight have been fully dumped. These eight phones store their BREW applications on the first memory bank, making them accessible. Unfortunately, the majority of AU phones store BREW applications on a separate memory bank that is significantly harder to reach. For example, the Toshiba W51H phone is partially dumped; its preloaded demo of Before Crisis: Final Fantasy VII is in a currently-unreadable user partition.
Metal Gear Solid Mobile Trial longplay by Kraze
A small number of preloaded and commercial EZweb games have been extracted. One notable game is the Japanese version of Metal Gear Solid Mobile, preloaded on a Sony-Ericsson W53S. Other dumped games include a mobile port of Biohazard 4 and the trial version of Dragon Quest III. Kraze says he has at least nine more AU phone models for research.
SoftBank Game Preservation
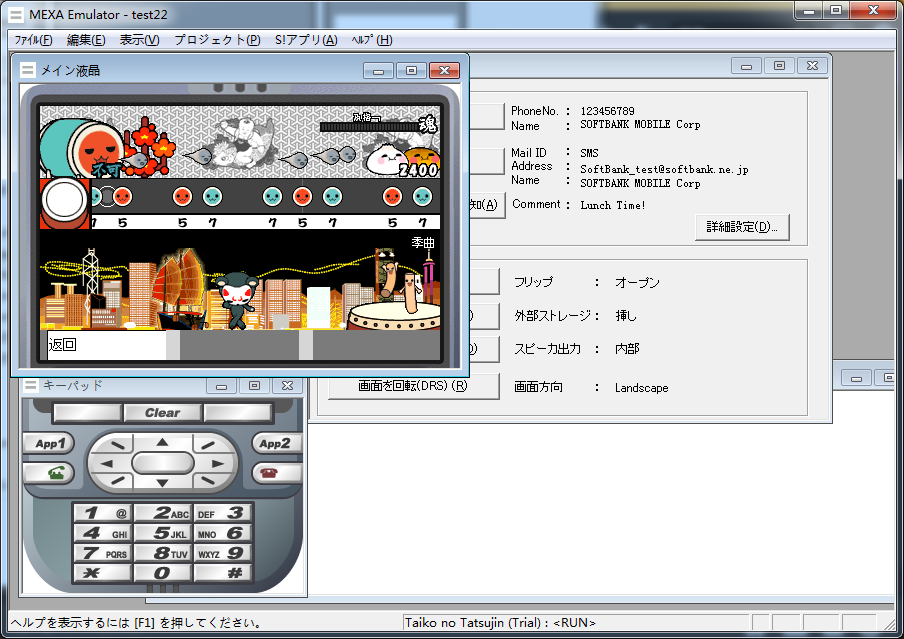
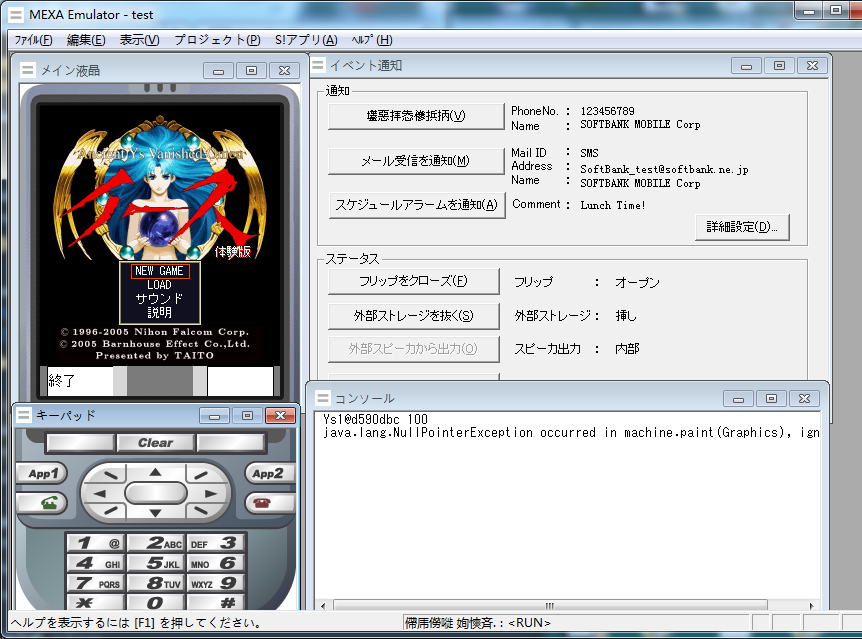
Dumped SoftBank games running in the MEXA emulator (image credit to LeonierX)
SoftBank phones face similar dumping challenges to DoCoMo phones, such as different phone models using different chips. However, all Samsung-made SoftBank phones use Qualcomm chips and are based on the SGH-Z series. There are known ways to access their filesystems, but the dumping tools have difficulty with the Samsung SoftBank phones' Japanese filenames, often crashing in the process. Some have hypothesized that SoftBank games can be easily dumped by simply being moved to a microSD card, but that method has not seen any success in practice.
As such, most preserved SoftBank games originate from Samsung models, although there are a few games that have been recently dumped from Panasonic models with the debug cable method. Some examples are a trial version of Ys 1 and a trial version of Taiko no Tatsujin from a Taiwanese 923SH.
The Challenge of Emulating Keitai Games
As of this writing, no comprehensive emulator exists for all types of keitai games. Each carrier used a different platform. DoCoMo's i-mode games ran on DoJa (later Star), a profile based on Java Micro Edition (JME). SoftBank games ran on MIDP J2ME with some custom API, making them closer to base J2ME. AU's EZweb games initially ran on Java (called EZplus games), but they quickly switched to Qualcomm's BREW platform in 2004. As such, the vast majority of games released on AU's mobile service are BREW-based. I will highlight the existing emulators for each platform.
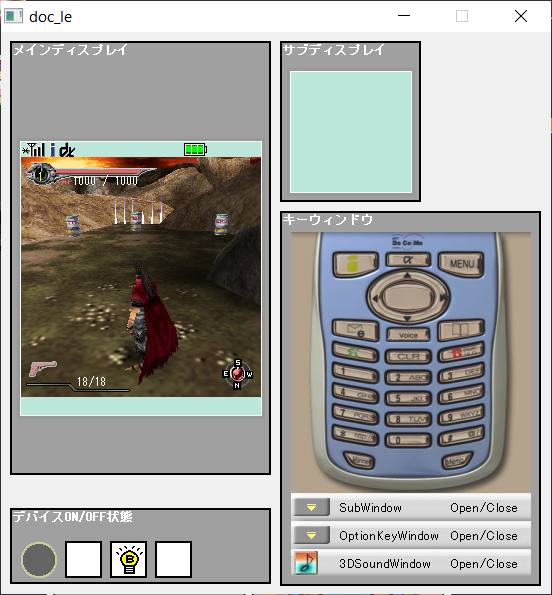
Currently, the only usable DoJa emulator is an emulator embedded inside the DoJa 5.1 SDK. This emulator has been useful to test recently-dumped i-mode games. Unfortunately, its emulation is not perfect by any means, experiencing performance issues with 3D games and even some 2D games. Furthermore, installing the emulator is a convoluted process, making it difficult to access for new users. Newly dumped games must also be modified to work with the SDK's emulator, a task undertaken by keen users like MemoryHunter.

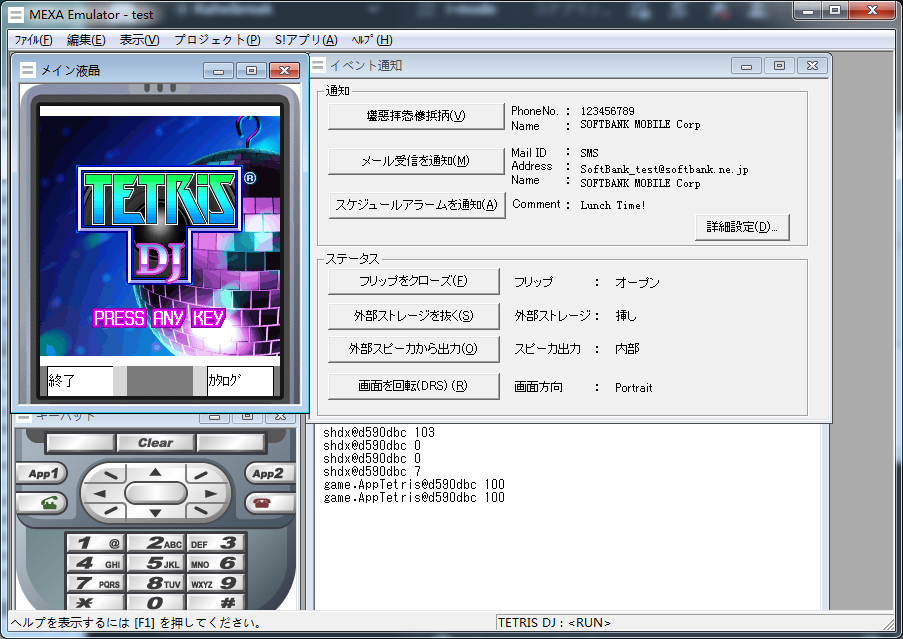
Left: Sonic Unleashed (Java) running in the J2ME Loader emulator. Right: Tetris DJ running in the MEXA emulator (image credit to LeonierX)
SoftBank games, despite their use of custom APIs, are closer to base J2ME than i-mode games. As such, emulation is more straightforward for SoftBank games. The J2ME Loader emulator is compatible with most J2ME games and even EZplus games. Kahvibreak user Torrenia is also gradually working on adding DoJa support to J2ME Loader, so there may be another option for i-mode game emulation in the future. There is also the MEXA emulator, which was a part of SoftBank's official mobile development SDK. It is not compatible with all SoftBank games, as it lacks FeliCa libraries.
Luckily, user XerTheSquirrel has been hard at work developing SquirrelJME, an all-inclusive Java virtual machine and RetroArch core. It would support DoJa games and SoftBank MIDP games alike, alleviating the emulation issues for both platforms. Xer has been making gradual progress since starting SquirrelJME in 2016, and the recent i-mode game dumps will give them more material to test with.
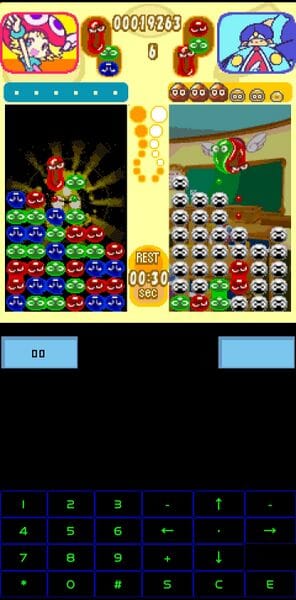
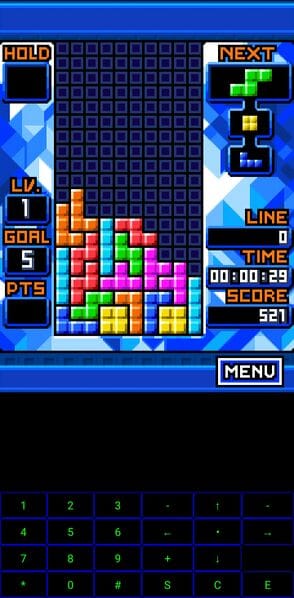

Puyo Puyo Fever DX, Tetris Blue, and Street Fighter 2 running in Melange. The left two games were dumped from Japanese AU phones.
Mobile BREW emulation is harder to come by. The only BREW emulator for mobile phones is Melange, singlehandedly developed by usernameak. While it is partially compatible with EZweb games, there is no sound support yet.
Keitai Game Documentation Efforts
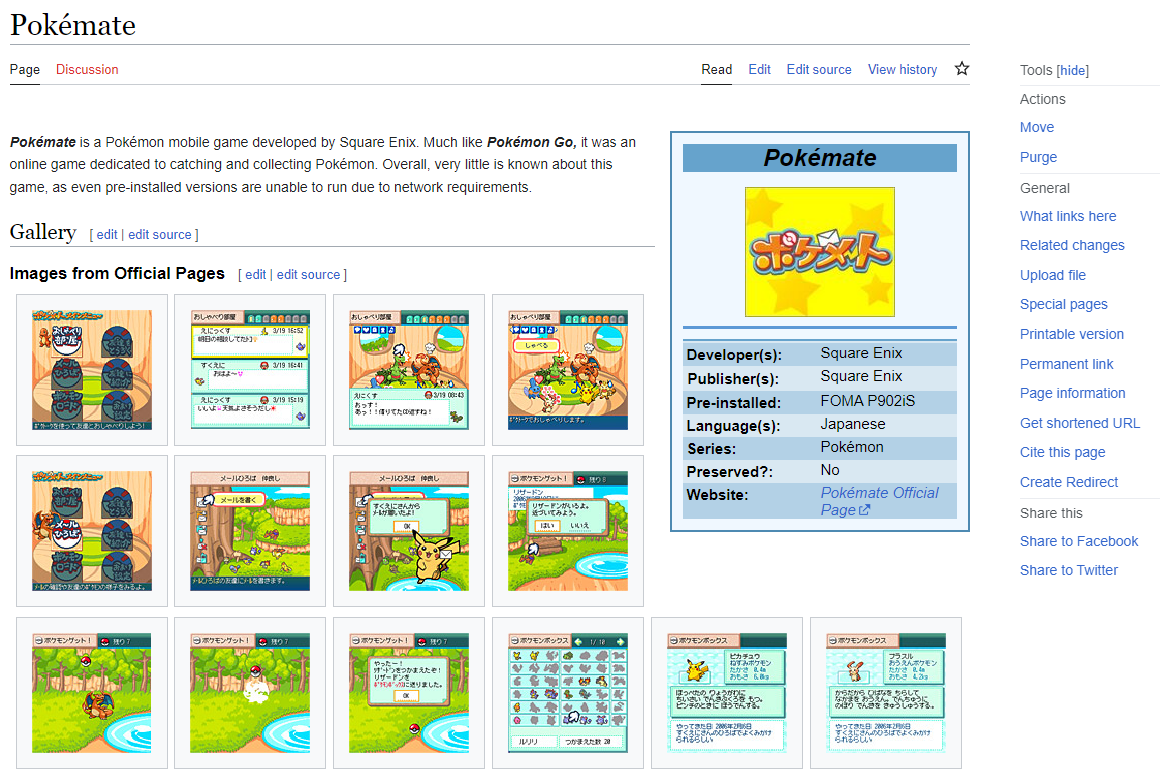
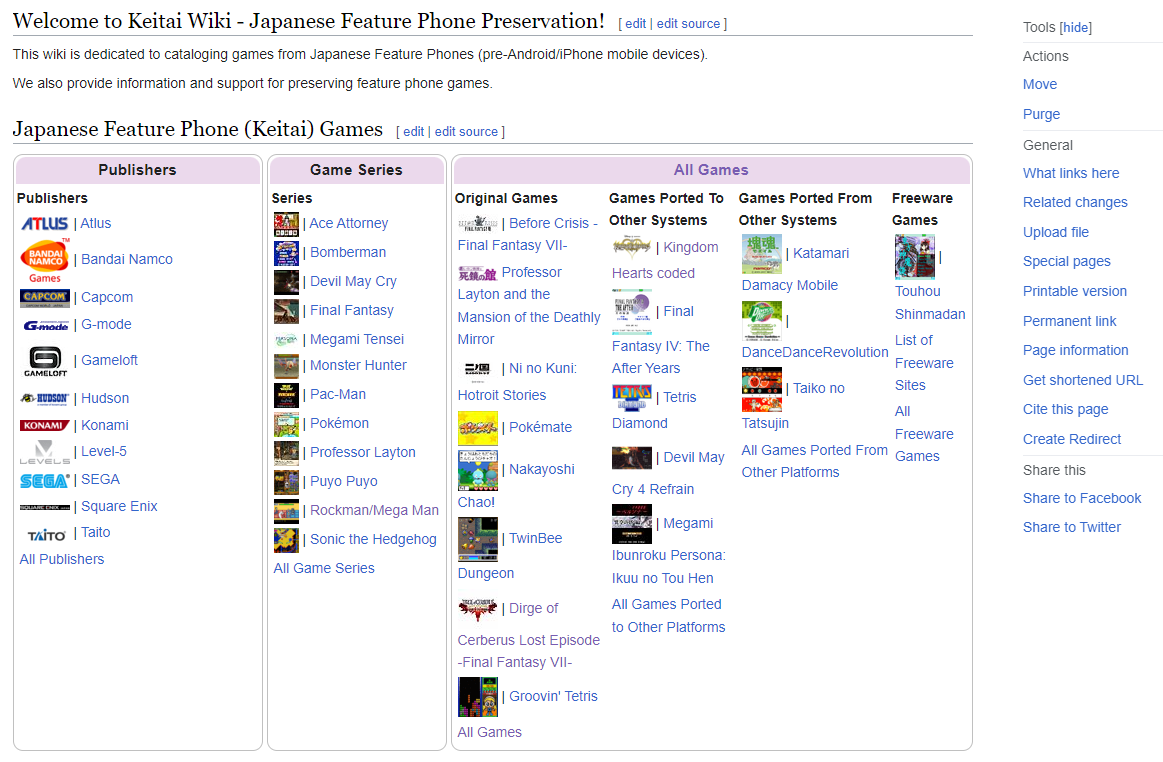
Keitai game preservation, being a very small sect of game preservation at large, did not have a centralized place to find information on games or their preservation. My Hit Save article from last year gave a broad overview of the games and preservation efforts, but it was by no means comprehensive. With three platforms, hundreds of games, and a variety of preservation methods, there needed to be a one-stop-shop for keitai game preservation resources.
This all changed in August, when user LNRC launched Keitai Wiki. Keitai Wiki aims to document keitai games, as well as the tools used to preserve them. Games are organized by publisher and series, with each page providing images, their preservation status, and archived links to their store pages. LNRC is the primary user working on the wiki, so it's still very much a work in progress. Nonetheless, Keitai Wiki is a great step in the right direction, and it will become an invaluable resource in due time.
Looking Towards the Future
As you can see, keitai game preservation has seen a great amount of progress in the last 12 months! We went from two dumpable DoCoMo phones in 2022 to over 50 as of this writing. The debug cable method has allowed for the preservation of commercial i-mode games, and encrypted i-mode game dumps on SD cards are finally readable for the first time. On December 29th, Xyz was able to dump and read a Fujitsu F-11C's filesystem after desoldering its NAND chip. This makes it the first DoCoMo Fujitsu to be dumped, opening the door for more Fujitsu phones. Thanks to Kraze's researching efforts, more EZweb games may be dumped down the line. Some SoftBank games have been preserved with the debug cable method, motivating users to look into their phones' internals.
Furthermore, there are other avenues of hacking that have yet to be studied in detail, namely software exploits. Many Japanese feature phones' web browser is an extremely old version of the NetFront Browser. This browser has already been cracked on handhelds like the Nintendo DS, meaning its version on Japanese feature phones is extremely susceptible to exploits. In addition, many of these phones use Flash Lite 3.1, a version of Flash that was successfully exploited to hack the Nintendo Wii. Such a hack will be complicated to pull off, but it is viable. Finally, user LNRC discovered an email draft exploit for DoCoMo phones. In short, file attachments for email drafts are encoded in Base64, meaning one could load a custom Base64 file on an SD card and paste it onto an email draft. This file could be an image, web bookmark, or even a Flash file. LNRC has theorized that a bookmark could trick the phone into showing its filesystem through a custom URL.
To say the future is bright would be an understatement! So many great advancements have been made in the past year, and there will undoubtedly be more in the next 12 months. I thank everyone who has spread the word of keitai game preservation, as well as those who have joined the preservation efforts. You all have played a role in helping the keitai game preservation community progress this far. I have linked resources below if you would like to see the game preservation progress firsthand. Special thanks to Asdf, Kraze, MemoryHunter, LNRC, usernameak, XerTheSquirrel, and Xyz for assisting me with writing this article. Here's to another year of keitai game preservation!
Resources
Dumpable Japanese feature phone models spreadsheet
DoCoMo debug cable method and DoJa SDK emulator setup guide
Donations towards Kraze's BREW game preservation work
KeitaiWiki Discord server (center for keitai game preservation)

